1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
70
71
72
73
74
75
76
77
78
79
80
81
82
83
84
85
86
87
88
89
90
91
92
93
94
95
96
97
98
99
100
101
102
103
104
105
106
107
108
109
110
111
112
113
114
115
116
117
118
119
120
121
122
123
124
125
126
127
128
129
130
131
132
133
134
135
136
137
138
139
140
141
142
143
144
145
146
147
148
149
150
151
152
153
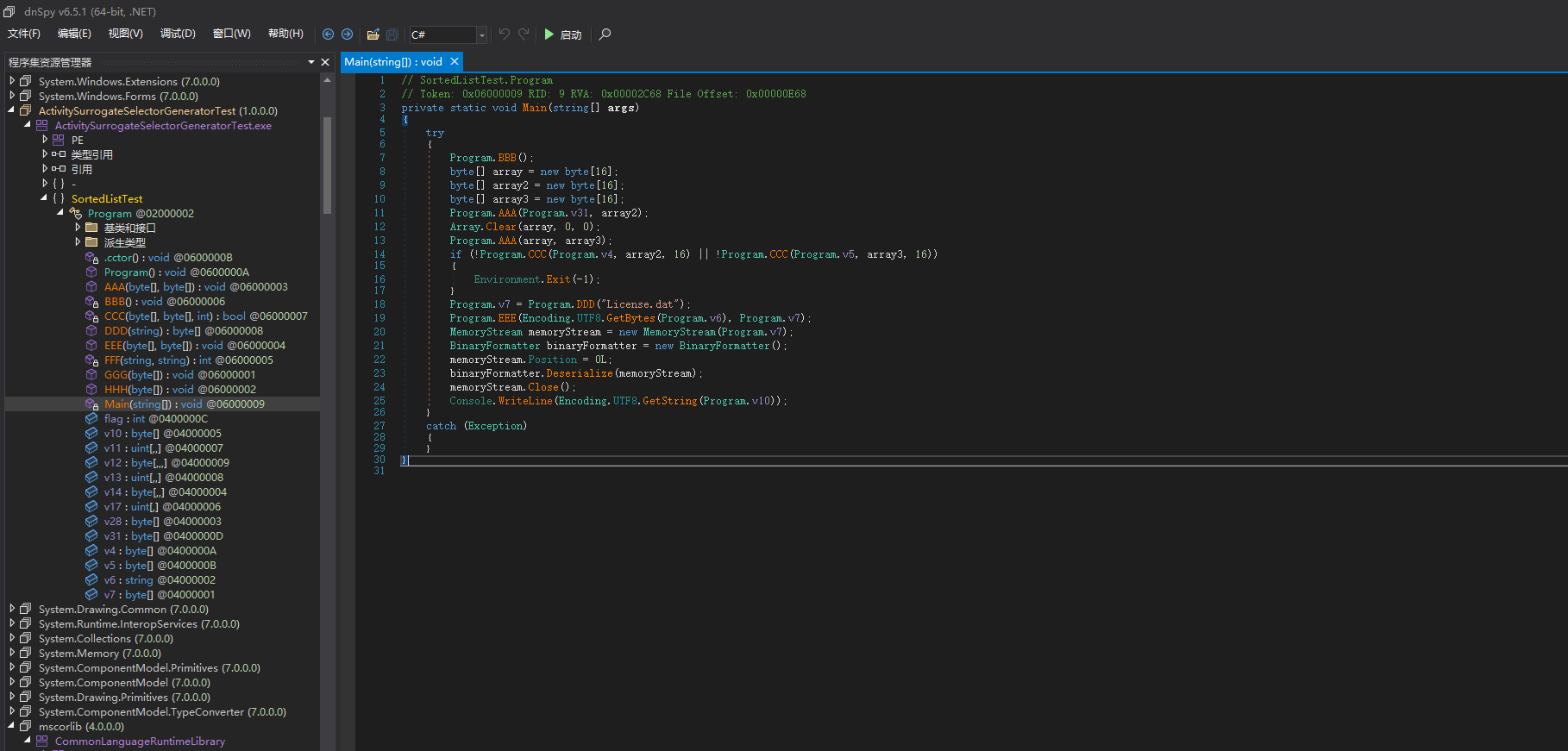
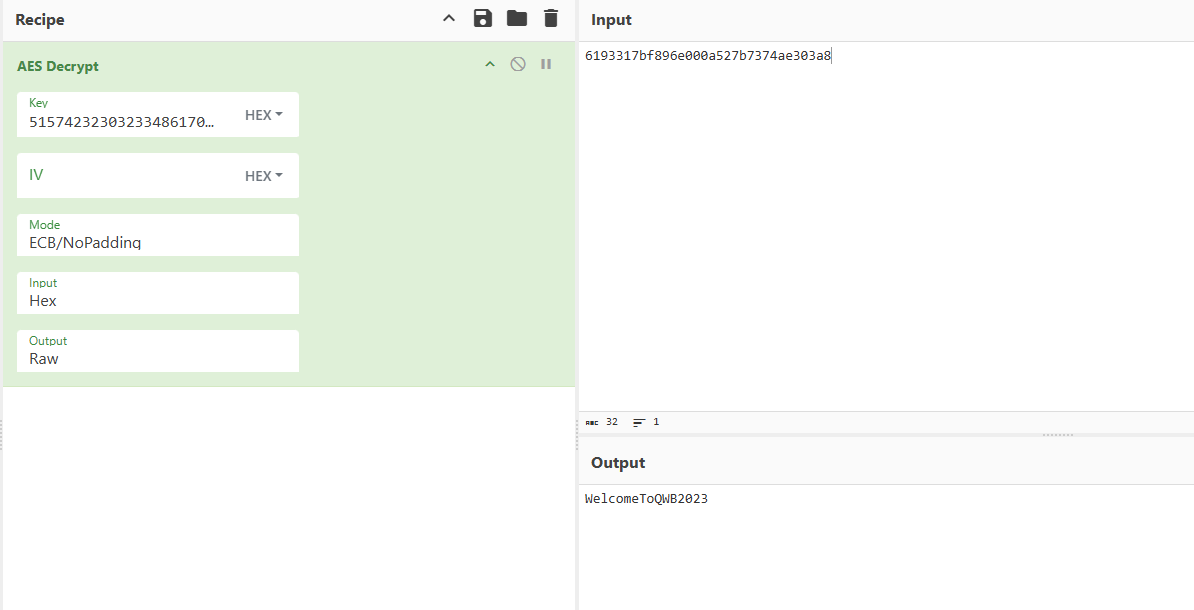
| using System;
using System.Collections.Generic;
using System.Text;
using System.IO;
public class Program
{
public static void GGG(byte[] v16)
{
byte[] array = new byte[16];
uint[] array2 = new uint[16]
{
0u, 5u, 10u, 15u, 4u, 9u, 14u, 3u, 8u, 13u,
2u, 7u, 12u, 1u, 6u, 11u
};
for (int i = 0; i < 16; i++)
{
array[i] = v16[array2[i]];
}
array.CopyTo(v16, 0);
}
public static void AAA(byte[] aaa, byte[] bbb, int randIndx, byte randByte)
{
for (int index1 = 0; index1 < 9; ++index1)
{
if (index1 == 8)
{
StringBuilder sb = new StringBuilder();
for (int i = 0; i < 16; i++)
sb.AppendFormat("{0:X2}", aaa[i]);
string round9Hex = sb.ToString();
Console.WriteLine($"ROUND9_BEFORE:{round9Hex}");
try
{
File.AppendAllText("round9_states.txt", $"{DateTime.UtcNow:O},{round9Hex}\n");
}
catch { }
if (randIndx != -1)
aaa[randIndx] = randByte;
}
Program.GGG(aaa);
for (int index2 = 0; index2 < 4; ++index2)
{
uint num1 = Program.v11[index1, 4 * index2, (int)aaa[4 * index2]];
uint num2 = Program.v11[index1, 4 * index2 + 1, (int)aaa[4 * index2 + 1]];
uint num3 = Program.v11[index1, 4 * index2 + 2, (int)aaa[4 * index2 + 2]];
uint num4 = Program.v11[index1, 4 * index2 + 3, (int)aaa[4 * index2 + 3]];
uint index3 = (uint)Program.v12[index1, 24 * index2, (int)(num1 >> 28) & 15, (int)(num2 >> 28) & 15];
uint index4 = (uint)Program.v12[index1, 24 * index2 + 1, (int)(num3 >> 28) & 15, (int)(num4 >> 28) & 15];
uint index5 = (uint)Program.v12[index1, 24 * index2 + 2, (int)(num1 >> 24) & 15, (int)(num2 >> 24) & 15];
uint index6 = (uint)Program.v12[index1, 24 * index2 + 3, (int)(num3 >> 24) & 15, (int)(num4 >> 24) & 15];
aaa[4 * index2] = (byte)((uint)Program.v12[index1, 24 * index2 + 4, (int)index3, (int)index4] << 4 | (uint)Program.v12[index1, 24 * index2 + 5, (int)index5, (int)index6]);
uint index7 = (uint)Program.v12[index1, 24 * index2 + 6, (int)(num1 >> 20) & 15, (int)(num2 >> 20) & 15];
uint index8 = (uint)Program.v12[index1, 24 * index2 + 7, (int)(num3 >> 20) & 15, (int)(num4 >> 20) & 15];
uint index9 = (uint)Program.v12[index1, 24 * index2 + 8, (int)(num1 >> 16) & 15, (int)(num2 >> 16) & 15];
uint index10 = (uint)Program.v12[index1, 24 * index2 + 9, (int)(num3 >> 16) & 15, (int)(num4 >> 16) & 15];
aaa[4 * index2 + 1] = (byte)((uint)Program.v12[index1, 24 * index2 + 10, (int)index7, (int)index8] << 4 | (uint)Program.v12[index1, 24 * index2 + 11, (int)index9, (int)index10]);
uint index11 = (uint)Program.v12[index1, 24 * index2 + 12, (int)(num1 >> 12) & 15, (int)(num2 >> 12) & 15];
uint index12 = (uint)Program.v12[index1, 24 * index2 + 13, (int)(num3 >> 12) & 15, (int)(num4 >> 12) & 15];
uint index13 = (uint)Program.v12[index1, 24 * index2 + 14, (int)(num1 >> 8) & 15, (int)(num2 >> 8) & 15];
uint index14 = (uint)Program.v12[index1, 24 * index2 + 15, (int)(num3 >> 8) & 15, (int)(num4 >> 8) & 15];
aaa[4 * index2 + 2] = (byte)((uint)Program.v12[index1, 24 * index2 + 16, (int)index11, (int)index12] << 4 | (uint)Program.v12[index1, 24 * index2 + 17, (int)index13, (int)index14]);
uint index15 = (uint)Program.v12[index1, 24 * index2 + 18, (int)(num1 >> 4) & 15, (int)(num2 >> 4) & 15];
uint index16 = (uint)Program.v12[index1, 24 * index2 + 19, (int)(num3 >> 4) & 15, (int)(num4 >> 4) & 15];
uint index17 = (uint)Program.v12[index1, 24 * index2 + 20, (int)num1 & 15, (int)num2 & 15];
uint index18 = (uint)Program.v12[index1, 24 * index2 + 21, (int)num3 & 15, (int)num4 & 15];
aaa[4 * index2 + 3] = (byte)((uint)Program.v12[index1, 24 * index2 + 22, (int)index15, (int)index16] << 4 | (uint)Program.v12[index1, 24 * index2 + 23, (int)index17, (int)index18]);
uint num5 = Program.v13[index1, 4 * index2, (int)aaa[4 * index2]];
uint num6 = Program.v13[index1, 4 * index2 + 1, (int)aaa[4 * index2 + 1]];
uint num7 = Program.v13[index1, 4 * index2 + 2, (int)aaa[4 * index2 + 2]];
uint num8 = Program.v13[index1, 4 * index2 + 3, (int)aaa[4 * index2 + 3]];
uint index19 = (uint)Program.v12[index1, 24 * index2, (int)(num5 >> 28) & 15, (int)(num6 >> 28) & 15];
uint index20 = (uint)Program.v12[index1, 24 * index2 + 1, (int)(num7 >> 28) & 15, (int)(num8 >> 28) & 15];
uint index21 = (uint)Program.v12[index1, 24 * index2 + 2, (int)(num5 >> 24) & 15, (int)(num6 >> 24) & 15];
uint index22 = (uint)Program.v12[index1, 24 * index2 + 3, (int)(num7 >> 24) & 15, (int)(num8 >> 24) & 15];
aaa[4 * index2] = (byte)((uint)Program.v12[index1, 24 * index2 + 4, (int)index19, (int)index20] << 4 | (uint)Program.v12[index1, 24 * index2 + 5, (int)index21, (int)index22]);
uint index23 = (uint)Program.v12[index1, 24 * index2 + 6, (int)(num5 >> 20) & 15, (int)(num6 >> 20) & 15];
uint index24 = (uint)Program.v12[index1, 24 * index2 + 7, (int)(num7 >> 20) & 15, (int)(num8 >> 20) & 15];
uint index25 = (uint)Program.v12[index1, 24 * index2 + 8, (int)(num5 >> 16) & 15, (int)(num6 >> 16) & 15];
uint index26 = (uint)Program.v12[index1, 24 * index2 + 9, (int)(num7 >> 16) & 15, (int)(num8 >> 16) & 15];
aaa[4 * index2 + 1] = (byte)((uint)Program.v12[index1, 24 * index2 + 10, (int)index23, (int)index24] << 4 | (uint)Program.v12[index1, 24 * index2 + 11, (int)index25, (int)index26]);
uint index27 = (uint)Program.v12[index1, 24 * index2 + 12, (int)(num5 >> 12) & 15, (int)(num6 >> 12) & 15];
uint index28 = (uint)Program.v12[index1, 24 * index2 + 13, (int)(num7 >> 12) & 15, (int)(num8 >> 12) & 15];
uint index29 = (uint)Program.v12[index1, 24 * index2 + 14, (int)(num5 >> 8) & 15, (int)(num6 >> 8) & 15];
uint index30 = (uint)Program.v12[index1, 24 * index2 + 15, (int)(num7 >> 8) & 15, (int)(num8 >> 8) & 15];
aaa[4 * index2 + 2] = (byte)((uint)Program.v12[index1, 24 * index2 + 16, (int)index27, (int)index28] << 4 | (uint)Program.v12[index1, 24 * index2 + 17, (int)index29, (int)index30]);
uint index31 = (uint)Program.v12[index1, 24 * index2 + 18, (int)(num5 >> 4) & 15, (int)(num6 >> 4) & 15];
uint index32 = (uint)Program.v12[index1, 24 * index2 + 19, (int)(num7 >> 4) & 15, (int)(num8 >> 4) & 15];
uint index33 = (uint)Program.v12[index1, 24 * index2 + 20, (int)num5 & 15, (int)num6 & 15];
uint index34 = (uint)Program.v12[index1, 24 * index2 + 21, (int)num7 & 15, (int)num8 & 15];
aaa[4 * index2 + 3] = (byte)((uint)Program.v12[index1, 24 * index2 + 22, (int)index31, (int)index32] << 4 | (uint)Program.v12[index1, 24 * index2 + 23, (int)index33, (int)index34]);
}
}
Program.GGG(aaa);
for (int index = 0; index < 16; ++index)
aaa[index] = Program.v14[9, index, (int)aaa[index]];
for (int index = 0; index < 16; ++index)
bbb[index] = aaa[index];
}
private static void Main(string[] args)
{
Random rand = new Random();
int targetIndex = 0;
int pairsToCollect = 16;
using (StreamWriter sw = new StreamWriter("pairs.txt"))
{
for (int i = 0; i < pairsToCollect; i++)
{
byte[] plain = new byte[16];
Array.Clear(plain, 0, 16);
byte[] state1 = new byte[16];
byte[] ct1 = new byte[16];
Array.Clear(state1, 0, 16);
Program.AAA(state1, ct1, -1, 0);
string sct1 = BitConverter.ToString(ct1).Replace("-", "");
byte faultByte = 0x00;
byte[] state2 = new byte[16];
byte[] ct2 = new byte[16];
Array.Clear(state2, 0, 16);
Program.AAA(state2, ct2, targetIndex, faultByte);
string sct2 = BitConverter.ToString(ct2).Replace("-", "");
string plainHex = BitConverter.ToString(plain).Replace("-", "");
sw.WriteLine($"{plainHex},{sct1},{sct2},{targetIndex:X2},{faultByte:X2}");
Console.WriteLine($"PAIR {i}: CT={sct1} FCT={sct2} idx={targetIndex} fb={faultByte:X2}");
targetIndex = (targetIndex + 1) % 16;
}
}
Console.WriteLine("Finished. pairs.txt written. Also check round9_states.txt for ROUND9_BEFORE logs.");
}
}
|